Streamline Your Desktop Operations and Improve Security with Amazon WorkSpaces - November 2016 Webinar Series | PPT

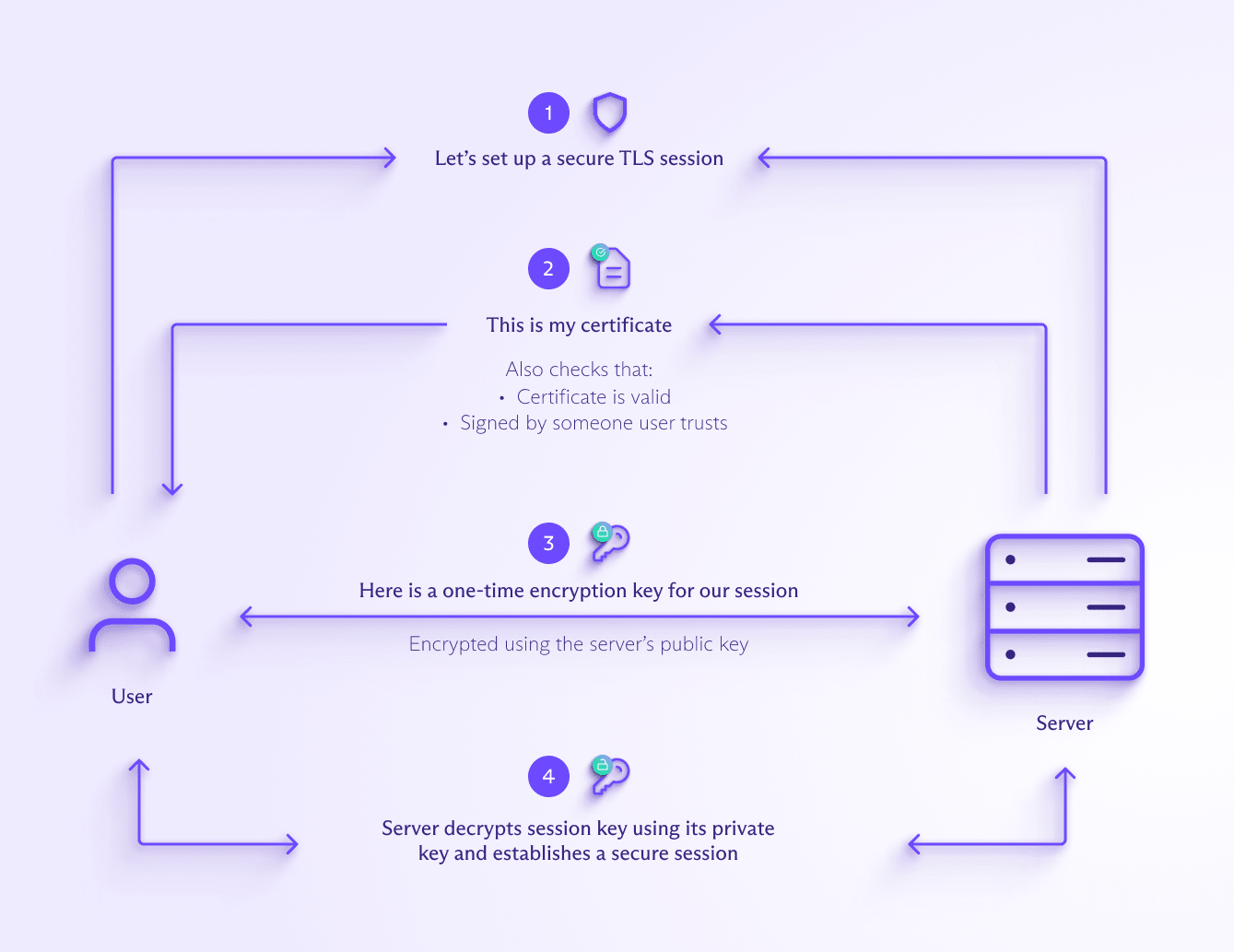
How encryption works in AWS: What assurances do you have that unauthorized users won't access your data? - FND310-R - AWS re:Inforce 2019 | PPT