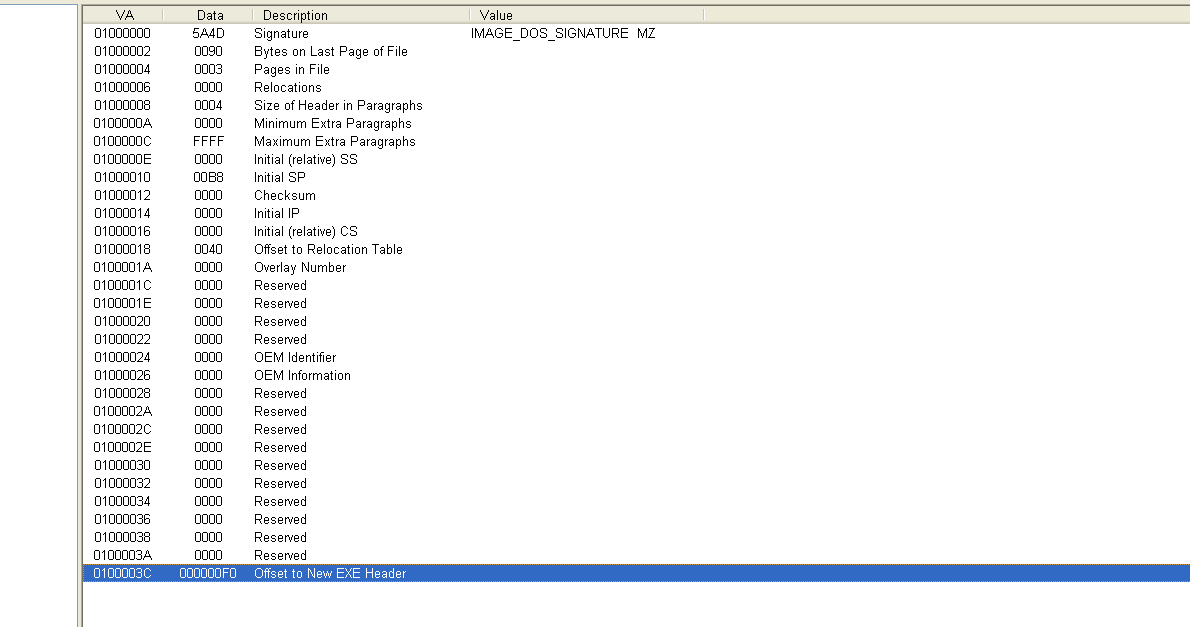
GitHub - cubiclesoft/php-winpefile: Windows Portable Executable file format command-line tools and PHP classes. Easily extract structures and information, modify files, and even construct files from scratch in the Windows Portable Executable (PE)

Getting to the root of the problem: A detailed comparison of kernel and user level data for dynamic malware analysis - ScienceDirect
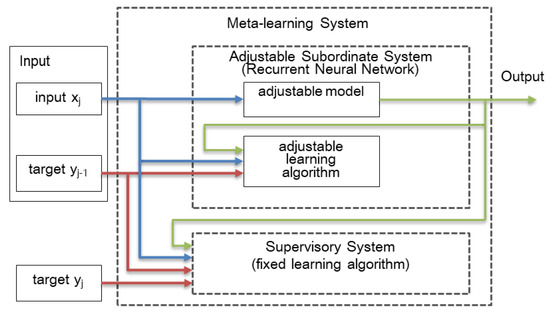
Information | Free Full-Text | MANNWARE: A Malware Classification Approach with a Few Samples Using a Memory Augmented Neural Network
GitHub - cubiclesoft/php-winpefile: Windows Portable Executable file format command-line tools and PHP classes. Easily extract structures and information, modify files, and even construct files from scratch in the Windows Portable Executable (PE)

Getting to the root of the problem: A detailed comparison of kernel and user level data for dynamic malware analysis - ScienceDirect
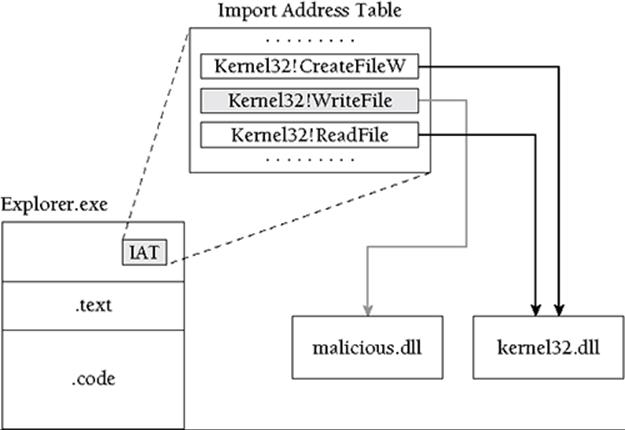

![Diverting functions in Windows with IAT patching | Yet Another [à compléter] Diverting functions in Windows with IAT patching | Yet Another [à compléter]](https://blog.neteril.org/wp-content/uploads/iat_patching/pe_format.png)
![4 Most Popular API Hooking Libraries [Comparison Guide] | Apriorit 4 Most Popular API Hooking Libraries [Comparison Guide] | Apriorit](https://www.apriorit.com/wp-content/uploads/2022/11/figure-2-6.png)



![Diverting functions in Windows with IAT patching | Yet Another [à compléter] Diverting functions in Windows with IAT patching | Yet Another [à compléter]](https://blog.neteril.org/wp-content/uploads/iat_patching/hopper-datasegment.png)